DNS over TLS is a big step in fixing a badly designed protocol, at least in terms of privacy, but it still leaves you having to trust the endpoint with all of that data that you are trying to keep private. While Cloudflare claims not to log your info or sell your data, you can never know for sure what’s going on at the far end.
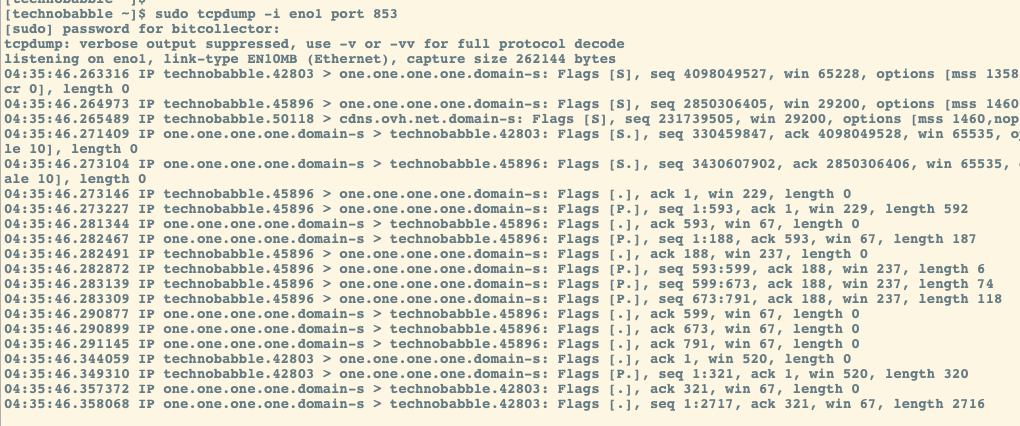
To that point, I’ve decided to send all of my DNS traffic over my self managed VPN that terminates on a server I rent in a Canada. This is an extra step I take to break the direct connection from my home IP address. In fact there are ZERO DNS packets leaving my home network, port 53 or 853.
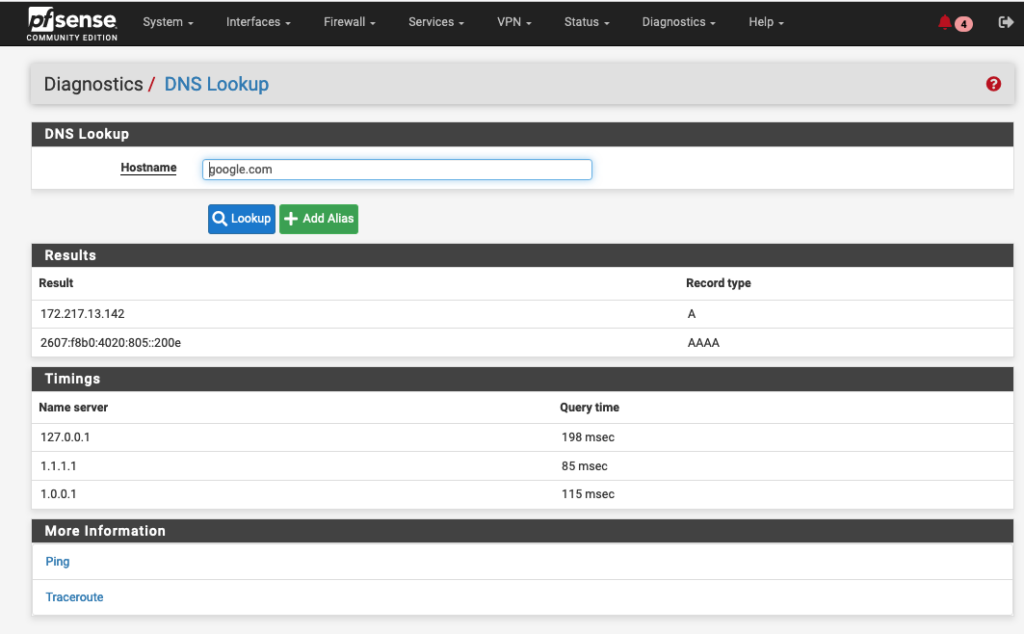
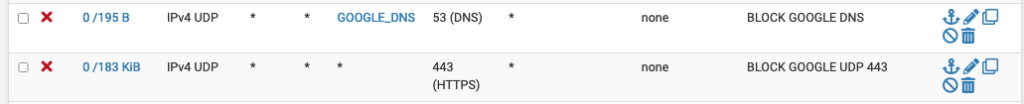
I’m running a DNS-TLS resolver on my pfSense firewall and connecting to 1.1.1.1 on port 853. I’m also explicitly blocking Google DNS 8.8.8.8/8.8.4.4 and QUIC protocol (UDP 443)
While my DNS lookup times suffer greatly, the resolver caches entries so only the initial lookup is slow.
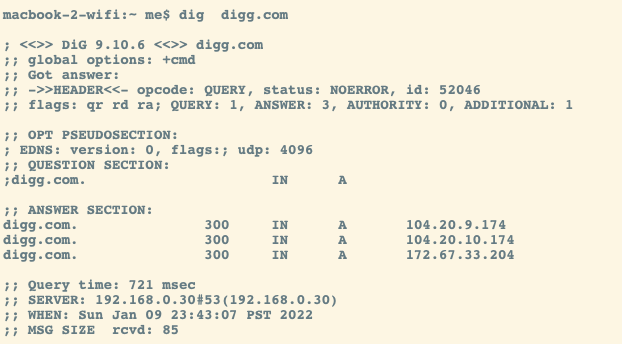
DNS Lookup to digg.com took 721 msec! (west coast to east coast and back)
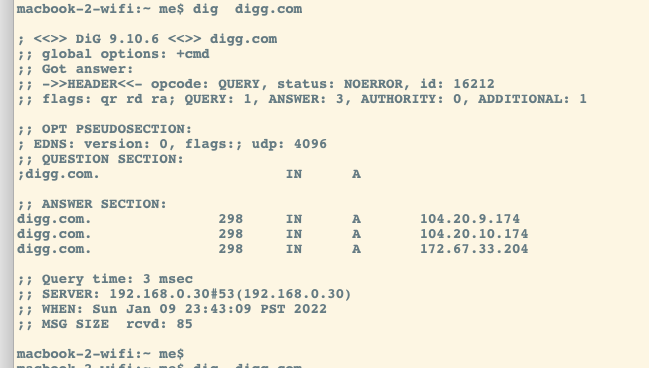
The following lookup took 3msec, much better!
Here are my pfSense settings where I’m sending the DNS over the VPN
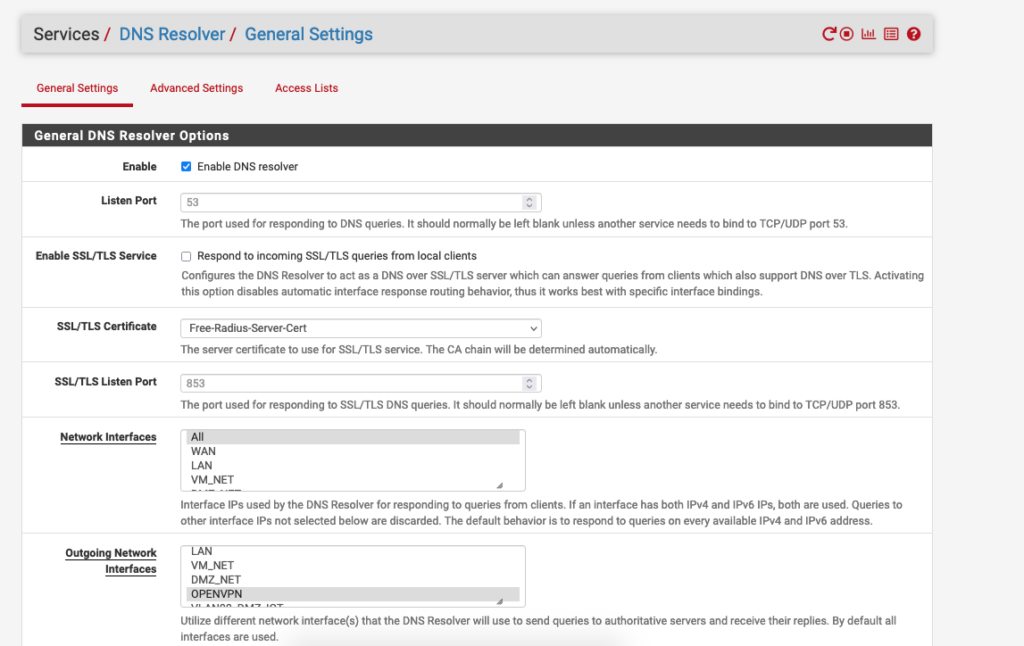
More DNS Resolver settings
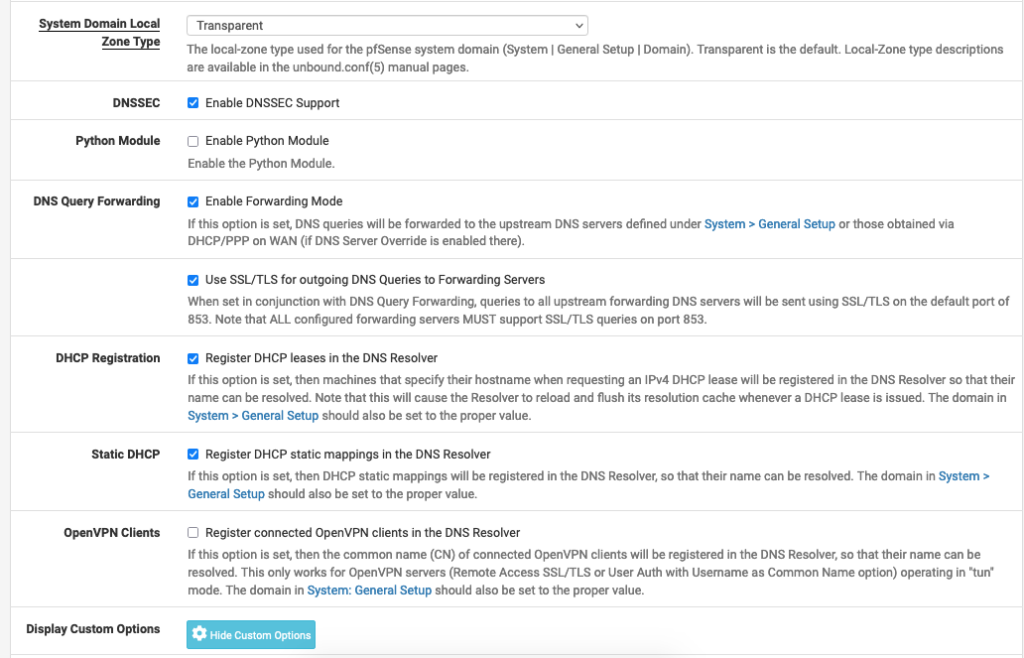
General DNS Settings:
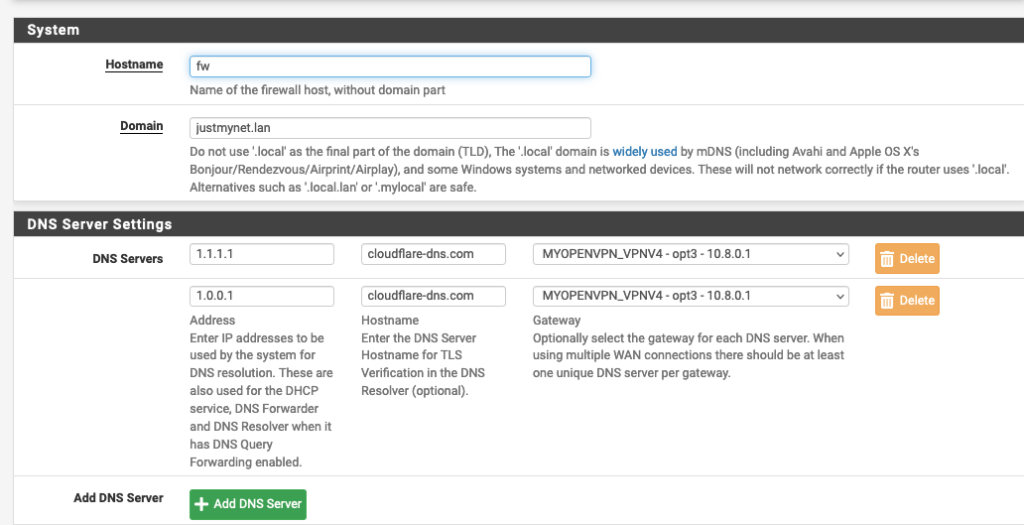
DNS Traffic exiting my VPN Server in Canada
Blocking Google DNS and QUIC with pfSense
Read more about DoT and DoH at Cloudflare:
https://www.cloudflare.com/learning/dns/dns-over-tls/
https://blog.cloudflare.com/handshake-encryption-endgame-an-ech-update/
